Cyber threats are no joke, but don’t worry, Managed Security Service Providers (MSSPs) are here to help! With the market booming, picking the right one can be tricky.
That’s where our guide comes in handy, steering you step-by-step to find the perfect cybersecurity match to protect your small business.
Whether you’re a startup or a big enterprise, we’ve got you covered, helping you navigate through your options with ease. Ready to dive in? Let’s go!
Skip to:
- What is a Managed Security Service Provider?
- MSSP Market Growth Projections
- Guidelines for Selecting an MSSP (7 Steps)

Custom image created in Canva
What is a Managed Security Service Provider?
A managed security service provider is an organization offering high-value security solutions and expertise for security systems, devices, and operations to external enterprises.
MSSPs employ sophisticated technologies and skilled cybersecurity personnel to manage clients' security functions.
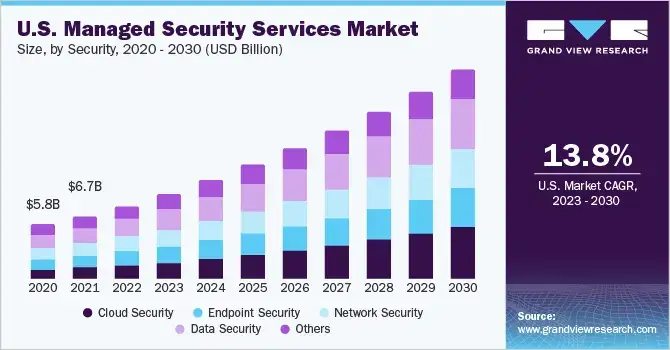
MSSP Market Growth Projections
- The global managed security services market is expected to achieve $77.01 billion by 2030. The CAGR (compound annual growth rate) is 12.8% from 2020 to 2030. (Source: Allied Market Research)
- North America's managed security services market is expected to jump from $13.82 billion in 2022 to $26.24 billion by 2027 at a CAGR of 13.8%. (Source: MarketsandMarkets)
Guidelines for Selecting an MSSP (7 Steps)
1. Conduct an internal security audit
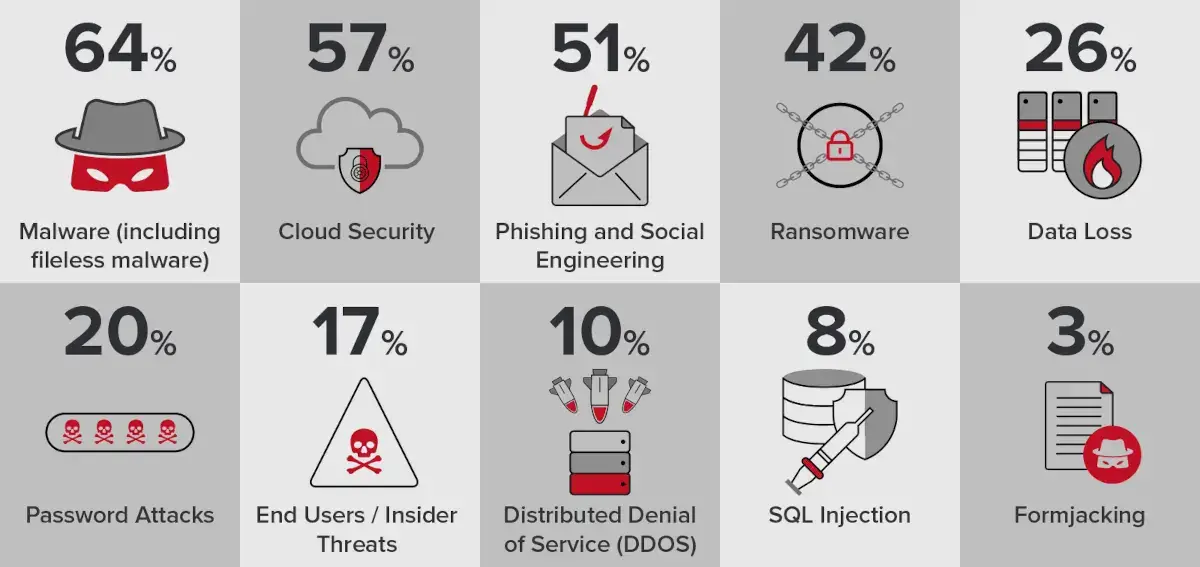
First, thoroughly evaluate existing security vulnerabilities within your systems and explicitly determine security requirements.
Closely examine crucial factors like compliance regulations, industry mandates, cyber risks, etc.
It enables identifying an MSSP that satisfies requirements. Clearly define needed services - network security, endpoint protection, audit reporting, penetration testing, threat intelligence, incident response, etc.
Specify any industry-specific needs like HIPAA compliance in healthcare.
- Identify all critical business systems, data assets, and infrastructure that need protection.
- Consult the compliance team and auditors to determine regulatory and compliance requirements.
2. Research prospective MSSP firms
Comprehensively search directories and seek recommendations to create a broad list of potential MSSP partners—target firms with expertise in your industry vertical and business scale.
Analyze their service capabilities, partnerships, credentials, and client references—Shortlist MSSPs equipped to deliver the required services per Step.
- Maintain a list of at least 3-5 firms for in-depth evaluation.
- Gather info on MSSPs from industry events, peer referrals, RFPs,
- Ensure MSSP has experience in your industry and with clients of similar size
3. Appraise MSSP capabilities
Critically evaluate shortlisted MSSPs across parameters like services offered, experience, expertise, infrastructure, scalability, flexibility, client satisfaction, etc.
Verify they can efficiently fulfill your defined security requirements. Inquire about specific experience delivering related managed security services.
Assess infrastructure, technologies, and processes for threat detection, incident response, compliance enablement, etc.
- Validate MSSP's capabilities match your requirements for services needed
- Ask for client case studies and references in your industry
4. Understand MSSP methodologies
Closely examine processes for threat monitoring, incident response, vulnerability management, audit reporting, and other relevant services. Review tools, technologies, and resources used.
Understand daily operations, use of automation, procedures for threat identification, escalation, incident containment, etc.
Also, assess staff experience levels, responsibilities, and security clearances.
- Request details on specific technologies and tools used by MSSP
- Ask about security processes, workflows, and automation capabilities
5. Compare MSSP billing models and contracts
Evaluate and compare MSSP costs based on your requirements, emphasizing value over just pricing. Meticulously review contract terminology and service level agreements.
Getting to grips with the ins and outs of ISO 27001 certification yourself is straightforward.
The basics of this framework are not too technically complex, yet have far-reaching implications in terms of the levels of protection afforded by an information security management system.
As such you must work with providers that are up to speed with its requirements as well.
Ensure a clear definition of deliverables like service scope, response times, metrics, liabilities, and insurance coverage.
Negotiate reasonable, predictable billing like monthly fees versus convoluted pricing models.
- Compare billing models - per device, user, incident, etc.
- Negotiate SLAs, downtime penalties, and liability limits favorable to you
6. Verify MSSP compliance and certification
Validate that the MSSP holds appropriate security certifications (e.g., ISO 27001), complies with regulations, follows best practices, conducts audits, etc.
Confirm that their systems and processes meet standards like PCI DSS HIPAA as applicable to you. Thoroughly corroborate compliance through audit reports and documentation.
- Review the latest independent audit reports for compliance
- Ensure certified for standards like ISO 27001, PCI DSS, HITRUST
7. Tour MSSP facilities
Visiting the MSSP's security operations center provides a first-hand perspective on capabilities.
Observe systems, processes, and staff in action—tour facilities to inspect infrastructure, physical security, and threat monitoring/response mechanisms.
Interact with personnel to evaluate experience, expertise, and professionalism.
- Meet the leadership team and frontline analysts during the facility tour
- Request live demos of security monitoring and incident response
Conclusion
Selecting a proficient MSSP is imperative for robust enterprise security. Perform extensive due diligence across parameters like experience, services, capabilities, methodologies, costs, compliance, and facilities.
It validates if the provider fulfills defined requirements and delivers maximum value.
Although time-intensive, it is an essential process for risk mitigation. Recommended best practices include:
- It is clearly defining internal security requirements.
- Exhaustively researching multiple candidate MSSPs
- Comparing service capabilities, credentials, and specializations
- Evaluating technology infrastructure, processes, and staff competencies
- Closely understanding operational and support methodologies
- Rigorously examining proposed contracts, costs, and billing models
- Verifying compliance, certifications, and audit trails
- Onsite inspection of facilities, technologies, and teams
A systematic, comprehensive MSSP selection process ensures choosing a trusted long-term security partner for your business.
The exhaustive evaluation provides dividends via an effective security solution protecting against the evolving cyber threat landscape.
Continual reviews and relationship management also remain critical for sustaining maximum value from the chosen MSSP.
Author Bio
Dmitry Kurskov, Head of the Information Security Department at ScienceSoft
An IBM Certified Deployment Professional, Dmitry has over 20 years of practical experience as an information and cybersecurity systems architect.
He manages the design and implementation of security policies and solutions within the company’s IT environment and oversees the delivery of managed security services to ScienceSoft’s clients.
Dmitry advocates the consistency and continuous improvement of cyber defense as the key to resisting ever-evolving cyber threats. He has significantly contributed to aligning ScienceSoft’s security management system with ISO 27001.