Data breaches have plagued companies, large and small, for several years.
*Updated 8/6/2024
As e-commerce companies, in particular, continue to collect more and more information about their customers, their risk of a data breach increases.
The consequences of a data breach can be devastating for a company. Not only could a breach destroy a company's reputation, but it could also result in costly litigation.
To mitigate the risk of a data breach, e-commerce companies must ensure they have information security policies and procedures in place.
What Constitutes a Data Breach
A data breach is a broad term used to describe unauthorized access to a company's systems, networks, and data. The unauthorized access could be the result of a cyber attack, employee error, or human error, among other things.
A data breach can occur when a company stores or transmits sensitive information, including employee and customer information, credit card numbers, and intellectual property. Data breaches occur in various forms and can have various consequences.
What Are The Consequences Of a Data Breach?
For most business leaders, the first thing that comes to mind is how it will affect their finances.
Depending on the type of data leak, this can be different, but most of the time, the victims have to pay for fixing the damage.
This could mean adding more security measures, looking into what happened, taking steps to stop the breach from spreading, paying people who were hurt, like customers, and paying legal fees.
You should prefer VPN free trial no credit card option to avoid any type of hurdle efficiently.
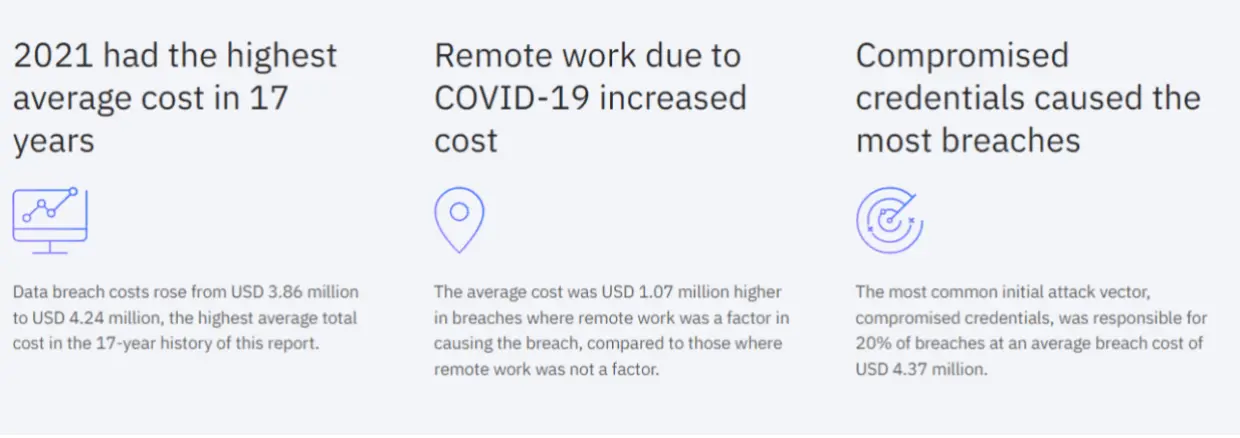
Image Source: IBM
Data breaches can also affect an organization's reputation in a way that is hard to fix and lasts for a long time.
After a breach, everyone is looking at you and waiting for answers, so it's important to make sure that each step that follows is taken correctly and on time. If not, the effects will keep getting worse, and you could lose customers, investors, employees, and more, both now and in the future.
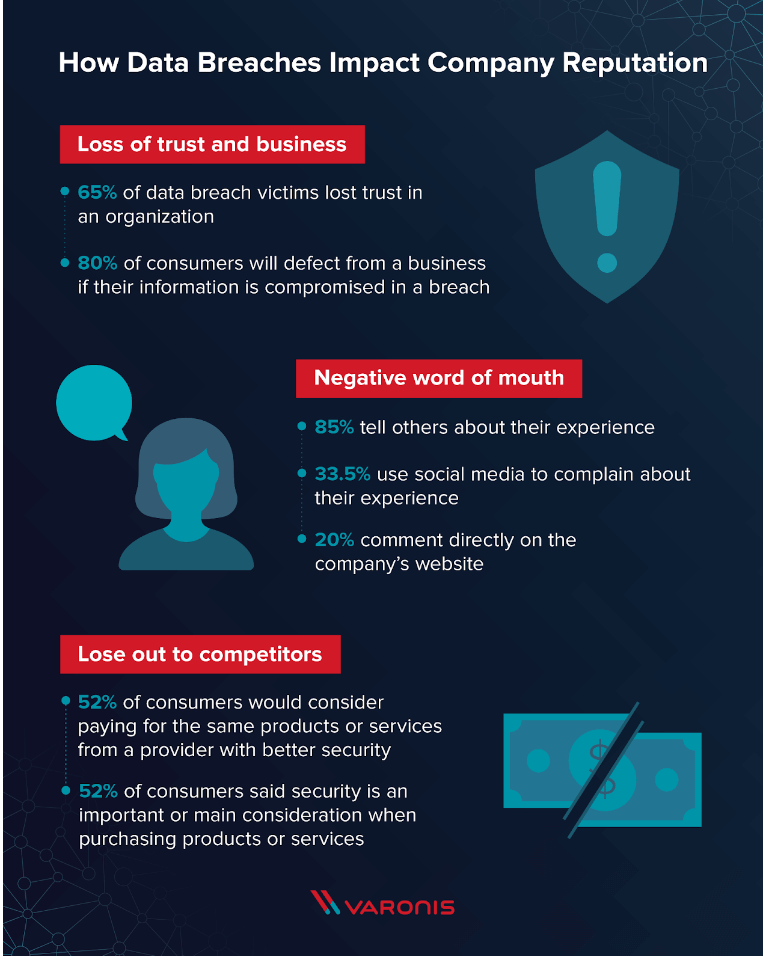
Image Source: Varonis
Depending on the severity of the breach, it may be necessary to stop all operations while the breach is being investigated and fixed.
This can take anywhere from a few days to a few weeks. This timeline can have a huge impact on both revenue and operations as a whole.
Regulations about data protection make it a legal requirement for organizations to make sure they do everything they can to stop a leak. This can even lead to class-action lawsuits when it comes to personal information.
How to Protect Customer Data
-
Implement data encryption
Encrypt your passwords and other critical information as a precaution in case the data is intercepted. Encryption codes the data so that it cannot be changed in its original form.
It's important to encrypt data at rest and data in motion, regardless of whether the information is being stored in physical or digital form. You should encrypt data wherever it lives, including in databases, hard drives, and files.
Image Source: Entrust
-
Back up and restore critical data
If a breach corrupts your website files or database, you can reduce downtime by restoring an older version of your website.
An excellent backup solution backs up your website files and database automatically for at least 30 days. Downtime on an e-commerce website is expensive, but it may be greatly reduced if you plan ahead of time to resume operations as soon as possible.
In this matter, implementing tokenization for data privacy can be a proactive step to safeguard sensitive customer information and maintain trust during unexpected disruptions.
-
Create a data retention plan
The risk of a data breach can be reduced by minimizing the amount of information you collect and how long you keep it.
The bare minimum necessary amount of identifying information is sufficient to allow customers to access their accounts.
Also, Google Sheets alternatives can be configured to store only essential customer data securely, aligning with data minimization practices and reducing the risk of data breaches while maintaining necessary account accessibility.
You can automate data retention by utilizing cloud archiving software that automatically purges data according to the schedule you set.
One method to consider when improving security is to build a private cloud. This provides you with a controlled environment where you have full authority over data management and protection.
-
Install an SSL certificate
This security precaution encrypts data as it travels from the user's browser to the payment processing site's server.
For example, if you take online payments through a gateway or third-party processor, an SSL certificate will protect hackers from obtaining payment information while it is in transit.
Image Source: ATAKDomain
-
Put in place a web application firewall
WAFs monitor traffic and prevent malicious attempts that might deplete your server's resources.
Look for a WAF and no logs VPN provider such as a free VPN, that complies with the Payment Card Industry Data Security Standards and has DDoS protection built-in.
Also, ensure that your WAF allows you to configure it to block all inbound traffic from countries where you do not ship.
If you don't ship outside of the United States, for example, configure your firewall to restrict traffic from anywhere outside of North America. This will assist to safeguard consumer data.
-
Rely on antimalware software
Automating malware detection and removal can improve your site's security and save you a lot of time.
Look for a thorough solution that examines your site's files and installs security fixes automatically. This will identify and remove malware from your website, which will give you one less thing to worry about on a daily basis.
-
Maintain plug-in up to date
A cybercriminal's best buddy is outdated plug-ins. Hackers are continuously looking for new weaknesses in popular e-commerce plug-ins. If you allow your site to function on outdated plug-ins on a regular basis, hackers will eventually find their way in.
-
Implement strong authentication
Retailers would be able to verify digital consumers by deploying multi-factor authentication (MFA).
To get access to the online account, the consumer must give two or more authentication elements. These elements could include a password, security questions, and a security token.
-
Employ a penetration test
A penetration test is an essential security step that will help identify any weaknesses in your website.
The test should be conducted by a cybersecurity professional, a penetration tester, or third-party firm with security expertise.
A penetration test will identify security holes before a malicious hacker does. The test will test the ability of a hacker to obtain access to your data.
-
Train employees on security awareness
It may come as a surprise to you that your staff is frequently the weakest link in the cybersecurity chain. However, a little security training might go a long way toward mitigating this danger.
Teach staff how to recognize the unusual activity, whether it's on your website or in phishing emails in their inboxes, and demonstrate what a good password looks like.
Image Source: KnowBe4
-
Teach customers about data security
Inspire your consumers to take a more active part in protecting their personal information.
It's important to let them know what information you get and how you gather it. Learn how to identify and report unusual activity on your website so that you can take action.
-
Create a response strategy
Prepare a cybersecurity incident response strategy in advance to help you respond quickly when a hacker breaches your defenses.
You may avoid the uncertainty and chaos that can ruin enterprises by explicitly stating who should do what following an assault. Regularly test your plan with cybersecurity exercises and repair any flaws you identify in your response plan.
Try Shift4Shop to launch your eCommerce business today.
Over to You
E-commerce companies carry a lot of risks. It's up to them to try to minimize the risks as much as possible. Still, no company can be 100% safe from hackers.
Companies should focus as much on prevention as they do on security since it's much easier to stop a breach than to deal with the consequences.
Author Bio
Alex is a passionate tech blogger, internet nerd, and data enthusiast. He is interested in topics that cover data regulation, compliance, eDiscovery, information governance and business communication.



