As an entrepreneur, taking steps to safeguard your business is essential. In the contemporary business world, physical and digital risks threaten any business's assets, reputation, and future success.
Understanding these threats and implementing a robust strategy to combat them is not an option but a necessity— that's the purpose of this piece. As you read this article, you'll learn insights from physical, digital, and internal threats to reinforce your business.
Take these steps, and your business will be far less likely to be compromised by a security breach.
Shortcuts:
- Understanding Business Security Basics
- Essential Security Measures
- Establishing a Business Continuity and Disaster Recovery Plan
- Hiring Security Professionals
- Legal and Compliance Aspects of Business Security
Understanding Business Security Basics
Business security is measures and strategies employed by a company to safeguard its assets. It involves protecting everything from physical assets like machinery or office equipment to intangible assets like intellectual property, customer data, and company reputation.
A robust security plan addresses physical, digital, internal, and external threats and implements protective measures to prevent and deal with such threats.
Source: Signix
Types of threats businesses face
The threats that can endanger a business will fall into several categories.
-
Cyber threats
Cyber threats are any potential or realized security breach which targets a business’s information system (digital software and hardware).
In our increasingly digital age, over 54% of SMEs have experienced some form of cyberattack over the past 12 months.
From phishing scams to ransomware attacks, annual cybersecurity breaches may cost companies as much as $10.5 trillion globally.
It's crucial for businesses to have a business insurance policy in place to mitigate the financial impact of such breaches.
-
Physical threats
Physical threats are security risks to physical property, such as theft, vandalism, or natural disasters, that can disrupt business operations or damage property.
Specialized insurance platforms like ContractorNerd can help business owners compare multiple quotes and secure tailored coverage that specifically addresses physical threats.
-
Internal threats
These threats come from within your organization. They could be intentional, like an employee stealing sensitive information, or unintentional, like an employee unknowingly opening a malicious email attachment.
-
External threats
External threats come from outside your organization, like competitors engaging in corporate espionage or criminals attempting fraud.
Potential consequences of inadequate security
On the surface, there's the risk of financial loss due to theft, fraud, or data breaches. Then there's the operational disruption, which could halt business processes and result in missed opportunities or lost revenue.
Moreover, reputational damage can negatively impact a business, with 60% of small companies closing within six months of a cyber attack.
It is mainly because consumers highly value their privacy and security, with even a single data breach damaging a company's credibility and customer trust beyond repair.
Understanding these basics is the first step to fortifying your business.
As we delve deeper into the essential security measures every entrepreneur should take, remember: your business's security is as strong as its weakest link. Aim for a comprehensive, well-rounded security plan that covers all bases.
Essential Security Measures
1. Physical security measures
If you operate out of an office or sell from a brick-and-mortar ship, ensuring the physical security of your business premises is fundamental to your overall security strategy. It involves safeguarding your assets, providing a secure environment for your employees, and handling certain payment types.
For example, knowing if a check is fake will save your business thousands of dollars. Here are some other key measures to consider:
-
Installation of surveillance cameras
Surveillance cameras act as your organization's eyes, constantly monitoring your premises. Ensure your cameras cover critical areas like entrances, exits, and areas where valuable assets or important documents are stored.
Also, consider adopting the likes of Bold Group alarm monitoring software so that security devices, including power-over-ethernet cameras, can be tracked and analyzed in real-time for enhanced security management, equipping you to respond to any event swiftly and decisively by responsible team members.
One effective approach is integrating a Coram AI camera system, which combines intelligent monitoring with advanced analytics to proactively detect threats and elevate on-site protection.
By integrating such solutions with unified endpoint management, you can ensure all devices are monitored and managed seamlessly, equipping responsible team members to respond to any event swiftly and decisively.
For businesses operating in low-light or nighttime environments, Coram’s night vision cameras offer an excellent solution. These advanced cameras provide clear visuals even in complete darkness, significantly boosting your after-hours security and deterring potential intruders.

Source: ButterflyMX
-
Secure locking systems
High-security locks and deadbolts offer the first line of defense against unauthorized access.
In recent years, electronic locks and keyless entry systems have gained popularity, allowing access only to individuals with the current codes or access cards.
These systems can be more secure and convenient, allowing you to control and monitor access to your premises easily.
-
Employee ID and access control
Implementing an employee identification system is essential in a secure business environment.
IDs allow for easy personnel identification, while systems like Automated Identity Verification can restrict unauthorized personnel from entering certain areas. It ensures that only individuals with the proper clearance can access sensitive areas, reducing the risk of internal threats.

Source: Avon
-
Regular security audits
Even the most robust security systems need regular check-ups. A security audit involves an assessment of your current security measures to identify any potential weaknesses or areas for improvement.
Ensure your systems are up-to-date, functioning correctly, and effectively protecting your assets. Additionally, assessing your automatic gate openers can significantly bolster physical security.
It's also crucial to check fire systems with advanced testing solutions to ensure they're functioning properly in case of emergencies.
For businesses considering updates or installations, evaluating systems like the Chamberlain vs Liftmaster wall mount offers insights into robust solutions tailored for modern security needs.
2. Cybersecurity measures
Depending on your type of business, cybersecurity risks, including ransomware protection, can be the most significant, as customer data and digital assets such as identity information and credit card details often form the backbone of many businesses.
Threat modeling can be particularly useful in addressing these risks by identifying potential threats and vulnerabilities. One highly effective approach is leveraging cloud application security testing to ensure robust protection for your business's applications and systems.
Knowing how to protect your business from cyber threats is essential. Additionally, using a decentralized VPN can improve security and privacy by spreading data across multiple servers.
You can also educate your team more effectively with free cybersecurity infographics that simplify complex concepts into easy-to-understand visuals.
-
Regular software updates and patching
Developers frequently update their software to address security vulnerabilities. Keeping your organization’s software up-to-date on an ongoing basis, coupled with robust patch management procedures, will help ensure your systems aren't left open to exploits that cybercriminals can leverage.
Be cautious about unsolicited contact from software developers, as tech support scams are an effective cyber attack.
For businesses striving to enhance their digital asset protection and streamline user account management efficiently, learning how to effectively implement SCIM support can be a game changer. This approach not only fortifies cybersecurity but also simplifies user access across various platforms.

Source: Clotech
-
Firewall and antivirus protection
By regulating incoming and outgoing network traffic, firewalls act as an entrepreneur's first defense against cyber-attacks.
If malicious programs make it through your firewall, antivirus programs protect your systems from malware that can steal, delete, or encrypt your data.
-
Data encryption
Encryption scrambles your data, turning it into a code that can only be deciphered with an encryption key. It means that even if a hacker manages to breach your data and obtain sensitive information without the encryption key, it’s worthless to them.
-
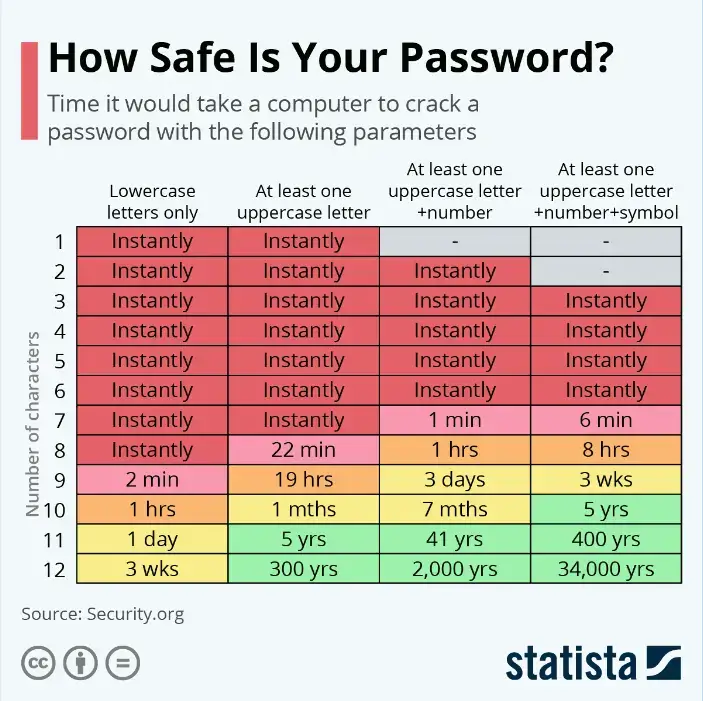
Secure password policies
Your business should have security policies requiring strong, unique passwords. These phrases combine uppercase and lowercase letters, numbers, and special characters.
Ensure your password policy has employees updating their passwords regularly and avoiding reusing them across multiple platforms.
Source: Statista
-
Two-factor authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of identification beyond just a password. It could be a fingerprint, a mobile app notification, or a unique code sent via text or email.
3. Internal security measures
As much as external threats pose a risk, internal threats can be just as damaging. A comprehensive security plan should include the following internal measures and be reinforced with comprehensive cloud-based security strategies to mitigate risks from all vectors:
-
Employee background checks
Before onboarding new employees, thorough background checks can provide valuable insights into their past behavior and reliability.
You can also use an online service or People Search API for SSN lookup to ensure accuracy and thoroughness. It can help mitigate potential risks and protect your company from internal threats.
-
Regular employee training on security best practices
An employee error can undermine even the most robust security measures. Regularly training employees on security best practices, from spotting phishing emails to safely handling sensitive data, can significantly reduce the risk of unintentional security breaches.
-
Secure document disposal procedures
Confidential documents should be disposed of securely to prevent sensitive information from falling into the wrong hands.
Implement procedures for shredding or securely erasing sensitive documents and data. Use a reliable Word to PDF converter whenever your documents are ready and finalized.
-
Protection against insider threats
Invest in best SaaS tools and policies that can help you monitor, detect, and respond to suspicious activities within your organization. It might include segregating duties, limiting access to sensitive information, and deploying insider threat detection software.
Establishing a Business Continuity and Disaster Recovery Plan
Emergencies and disasters are unpredictable, but your response to them doesn't have to be.
A well-crafted Business Continuity and Disaster Recovery Plan (BCDR) can be your company's lifeboat when navigating the stormy seas of unforeseen incidents.
-
Importance of business continuity and disaster recovery plans
A BCDR plan outlines the procedures and instructions an organization must follow in the face of such incidents.
Its goal is twofold: ensure the continuity of business operations as much as possible during the incident (Business Continuity), and recover critical functions after the incident has passed (Disaster Recovery).
I cannot overstate the importance of a BCDR plan. It minimizes the impact of disasters on business operations, helps maintain customer trust, and ensures the business's long-term survival.
With such a plan, the company may avoid prolonged downtime, loss of revenue, and in worst cases, complete shutdown.
-
Steps to create a continuity and recovery plan
- Risk Assessment: Identify the threats and vulnerabilities that could impact your business. Understand the potential impact of these risks to prioritize your planning efforts.
- Business Impact Analysis: Analyze your business processes to determine which are critical for the survival of your business. Understand their operational and financial impact if disrupted.
- Resource Identification: Identify the resources required to restore and maintain critical business functions during a disaster, including personnel, information, equipment, financial allocations, and infrastructure.
- Plan Development: Create procedures to manage and recover from the impact of a disaster. Delineate the roles and responsibilities of all involved parties.
- Communication Plan: Develop a communication strategy to inform all stakeholders during a crisis. It includes employees, clients, vendors, and the media.
-
Testing and updating the plan
A BCDR plan is not a one-and-done project. Test it regularly to identify potential flaws and areas for improvement. Simulated drills and exercises can provide invaluable insights into the effectiveness of your plan.
Moreover, update your plan as your business grows or changes. It includes changes in personnel, processes, technologies, or physical locations. An outdated plan can be as ineffective as no plan at all.
Hiring Security Professionals
Entrepreneurs should consider hiring security professionals, such as GuidePoint Security, when they recognize the complexity of safeguarding their business assets exceeds their current capacity or expertise.
Staying ahead of potential risks requires specialized knowledge and experience in today's rapidly evolving threat environment. Security professionals can help to:
- Identify vulnerabilities in your current security measures.
- Develop and implement robust security strategies.
- Provide ongoing monitoring and quick response to security incidents.
- Train your team on security best practices.
- Ensure compliance with industry-specific security regulations.
The decision to hire security professionals underscores an important recognition—that the security of your business is a critical aspect of your overall business strategy, requiring expert

